IP Spoofing or IP address spoofing is a form of cyber attack in which the attacker tries to deceive a network system into believing that data comes from a trusted source. This prompts the user to trust that unknown host, often giving the attacker access to private data and sensitive information.
You can detect IP spoofing by:
- Implementing filtering of both inbound and outbound traffic.
- Configuring your router to reject packets coming from outside your trusted network.
- Enabling encryption on your router.
- Use IPv6 as opposed to IPv4.
- Secure websites with HTTPS protocols.
- Install a trustworthy antivirus.
In this article, I will provide a comprehensive guide on detecting IP spoofing and discuss prevention strategies.

Table of Contents
How to Detect IP Spoofing?
Below are some methods which you can use to detect IP Spoofing:
- Monitoring network traffic for irregular patterns or inconsistencies can help identify potential spoofing attempts. For example, look for multiple packets with the same source IP address but different TTL (Time to Live) values or a sudden spike in traffic from a specific IP address. You can also search for packets with source addresses that don’t match the expected range of valid addresses from known hosts on the network or those outside it (for example, if there are no computers with an IP address beginning with 192).
- Network administrators can also use tools such as firewalls and intrusion detection systems (IDS) to help identify potential threats and block them before they cause damage to the system or network infrastructure.
- Another method is cross-referencing the geolocation of incoming packets with the expected location of the source IP address. As stated above, significant discrepancies between the two locations may indicate a spoofed IP address.
- The last method is to check logs. Most devices keep logs of all the packets sent and received. Reviewing past logs may help rule out any anomalies, such as a large number of packets being sent from a single IP address.
How Does IP Spoofing Work?
As the name suggests, IP spoofing is a malicious technique cyber criminals use to impersonate another device user or network. Spoofing is made successful by exploiting the vulnerabilities of Internet Protocols (IP).
Here is how IP Spoofing works:
- Every device connected to the Internet is assigned a unique IP address, which acts as its identifier. IP addresses are formatted as four groups of numbers (IPv4) or eight groups of numbers and letters (IPv6), separated by periods or colons, respectively.
- Next, we have ‘packets,’ consisting of the header and the payload. The header contains essential information, such as the source and destination IP addresses, while the payload contains the actual data being transmitted.
- When an attacker tries their spoofing technique, They are essentially trying to modify the source IP address in the header of an IP packet so that you, as a user, think that this packet is coming from a different/trusted device.
- Once an attacker has successfully injected a spoofed IP packet into a network, they can exploit it for various purposes like DDoS attacks, MITM attacks, and evading authentication-based IP systems.
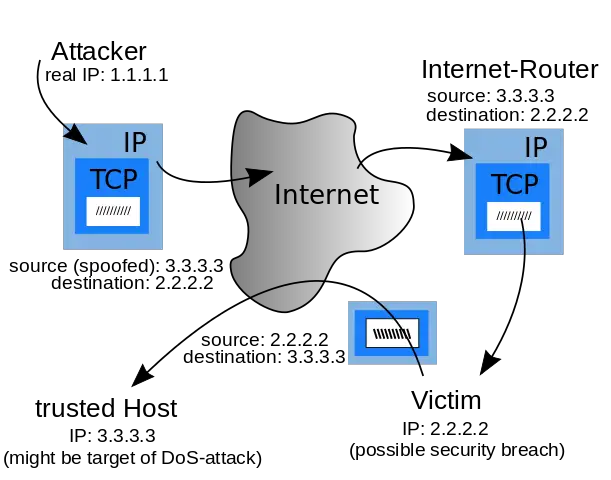
Types of Spoofing
- Non-Blind Spoofing: In this type, the attacker resides on the same subnet as the target, allowing them to intercept replies and maintain an active connection. This proximity gives the attacker a distinct advantage, as they can easily monitor the traffic and gather crucial information to craft tailored attacks.
- Blind Spoofing: Contrarily, blind spoofing occurs when the attacker is located outside the target’s subnet. Due to their distant position, the attacker relies on guesswork to predict sequence and acknowledgment numbers, making establishing and maintaining connections harder. Despite the challenges, blind spoofing is still used for DDoS attacks and one-way data manipulation.
- Direct Spoofing: This type of IP spoofing involves a direct attack on the victim’s device. The attacker forges the source IP address to masquerade as a trusted entity, gaining unauthorized access or stealing sensitive information.
- Indirect Spoofing: In indirect spoofing, the attacker targets a third-party device and manipulates it to bombard the victim with excessive traffic. This type is commonly seen in reflection or amplification attacks, where the attacker leverages a vulnerable intermediary to amplify the impact of their actions.
Common Attacks Due to IP Spoofing
Botnets
Botnets, networks of compromised devices controlled by cybercriminals, are often employed to launch large-scale attacks. IP spoofing allows attackers to mask the true origin of botnet traffic, making it challenging for security professionals to trace back the source and mitigate the threat effectively.
Address Resolution Protocol (ARP) Poisoning
ARP poisoning is an attack that exploits the ARP protocol, which translates IP addresses into physical addresses (MAC addresses) on a local network. Cybercriminals use IP spoofing to impersonate a trusted device on the network, sending malicious ARP messages to update the target’s ARP cache. Consequently, the target device sends its data to the attacker instead of the legitimate destination, allowing for data interception and manipulation.
Domain Name System (DNS) Spoofing
DNS spoofing, also known as DNS cache poisoning, is an attack where cybercriminals exploit the DNS protocol to redirect users to malicious websites. Attackers use IP spoofing to impersonate a legitimate DNS server, sending falsified DNS responses to the target. As a result, the target unknowingly accesses a malicious website, potentially exposing sensitive information or falling victim to malware infections.
Man-in-the-Middle (MITM) Attacks
MITM attacks involve an attacker intercepting communication between two parties by spoofing one or both of their IP addresses. This enables the attacker to eavesdrop on the conversation, modify transmitted data, or inject malicious content. When combined with IP spoofing, the complexities and burstiness of MITM attacks make them particularly challenging to detect and counteract.
Preventing IP Spoofing
If you are an IT specialist who works in cyber-prevention, then you can use the following methods to prevent spoofing:
- Use encryption and authentication
- Implement access controls
- Monitor network traffic
- Use key-based authentication for unknown sources
As for end users, who do not have the technical expertise to implement such methods, some of the easiest ways to keep such attacks at bay include updating your software regularly, using antivirus software, and avoiding interaction with spam emails and attachments.
Conclusion
In conclusion, IP spoofing poses a significant threat to both organizations and individuals, enabling attackers to conceal their identities and carry out malicious activities. However, by understanding the various types of attacks and implementing effective detection and prevention strategies, users can better protect their digital assets and mitigate the risks associated with IP spoofing.
Thank you for reading.

Leave a Reply